WannaCry
Ransomware Cryptoworm
MALWARE
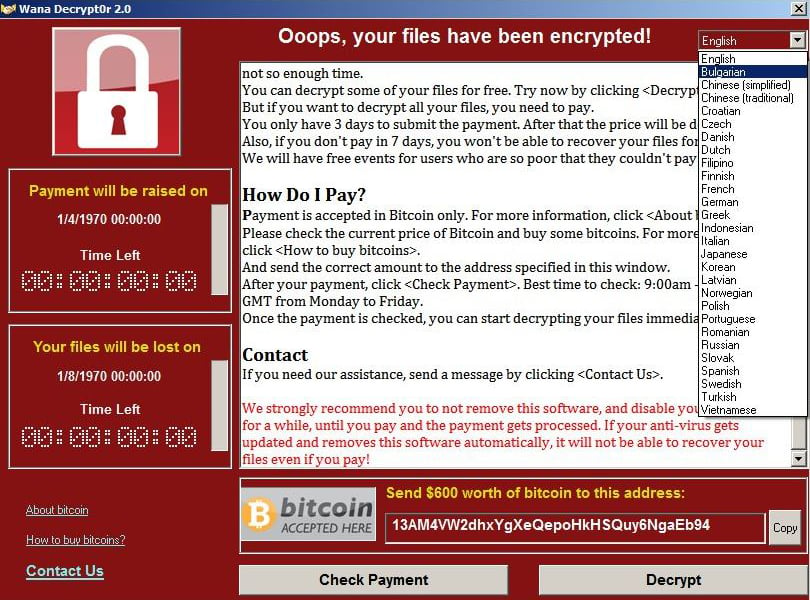
The advent of cryptocurrencies, more specifically Bitcoin, made a lot of people very rich. But like all new technologies, it also came with its share of malicious actors. If it wasn't the rampant drug markets profiting from the 'privacy' of the digital coin, it was the 'crypto-ransomers' (double entendre here) taking advantage of a new form of collection. You see, one of the key things that makes ransomware so easy to proliferate is the lack of a paper trail of said money reaching the ones holding you hostage.
In 2017 the price of Bitcoin had exploded to its then all-time high, up more than 10,000% from its original price at its inception of trading on the market. Also in 2017, the world witnessed the unprecedented spread of the WannaCry ransomware, malicious software that wreaked havoc on computer systems all over the world. The rise of the latter not only exposed widespread vulnerabilities in outdated software but also exacerbated the urgent need for enhanced cybersecurity measures. You could say it was a real eye-opener for a lot of businesses and individuals.
The attack exploited a vulnerability in Microsoft's Windows operating system, particularly targeting systems running outdated versions that had not been patched with the necessary security updates. Many of the businesses that were affected stated that one of the reasons that security patches were not installed was due to a need for the systems they were running on to have 24/7 operation - bringing them offline was too costly to their operation, a move which would end up costing them significantly more.
The attack was estimated to have affected more than 300,000 computers across 150 countries within a matter of days, with the total damages up to billions of dollars in total. Its success was attributed to its ability to exploit a vulnerability known as 'EternalBlue'. This malware was developed by the United States National Security Agency (NSA) and was stolen and leaked by a hacking group called the Shadow Brokers.
The extent of the malware was brutal. Due to the nature of the beast, it spread like wildfire, affecting critical infrastructure, healthcare systems, and businesses, disrupting operations, and causing financial losses. Said beast was a form of worm, which self-replicates and spreads to other vulnerable machines on its own accord. Although the attack only lasted for 4 days, the extent of the damage was significant.
So what did the world learn from this and what can we do to prevent a repeat of this? The attack served as a wake-up call for governments, organizations, and individuals. It highlighted the importance of regular software updates, especially for those critical security patches that are frequently rolled out to combat these things, as Microsoft and the like keep well informed of new threats. It also emphasized the need for a broader look at robust cybersecurity practices. Organizations that had failed to update their systems in a timely manner bore the brunt of the attack, facing significant operational disruptions and reputational damage. Any business that is especially used to 24/7 operation, would feel the heat more than most others.
In our daily lives as smaller businesses or even individuals, it is still a key lesson to be learned - that those pesky 'Microsoft needs to update' messages may actually serve a very important purpose. To keep your data available and accessible and keep you out of the grasp of cybercriminals.
